Unlockt Me Bypass iPhone, a term that sparks both curiosity and concern, refers to methods and tools that aim to circumvent the robust security measures implemented by Apple on iPhones. This concept raises questions about the potential vulnerabilities of these devices, the ethical implications of bypassing security, and the potential consequences for users and their data.
Unlockt Me bypass tools might employ various techniques, such as exploiting software flaws, manipulating system settings, or using brute force methods to gain unauthorized access. However, the risks associated with these methods are significant, potentially leading to data breaches, privacy violations, and even legal repercussions.
Understanding “Unlockt Me Bypass iPhone”
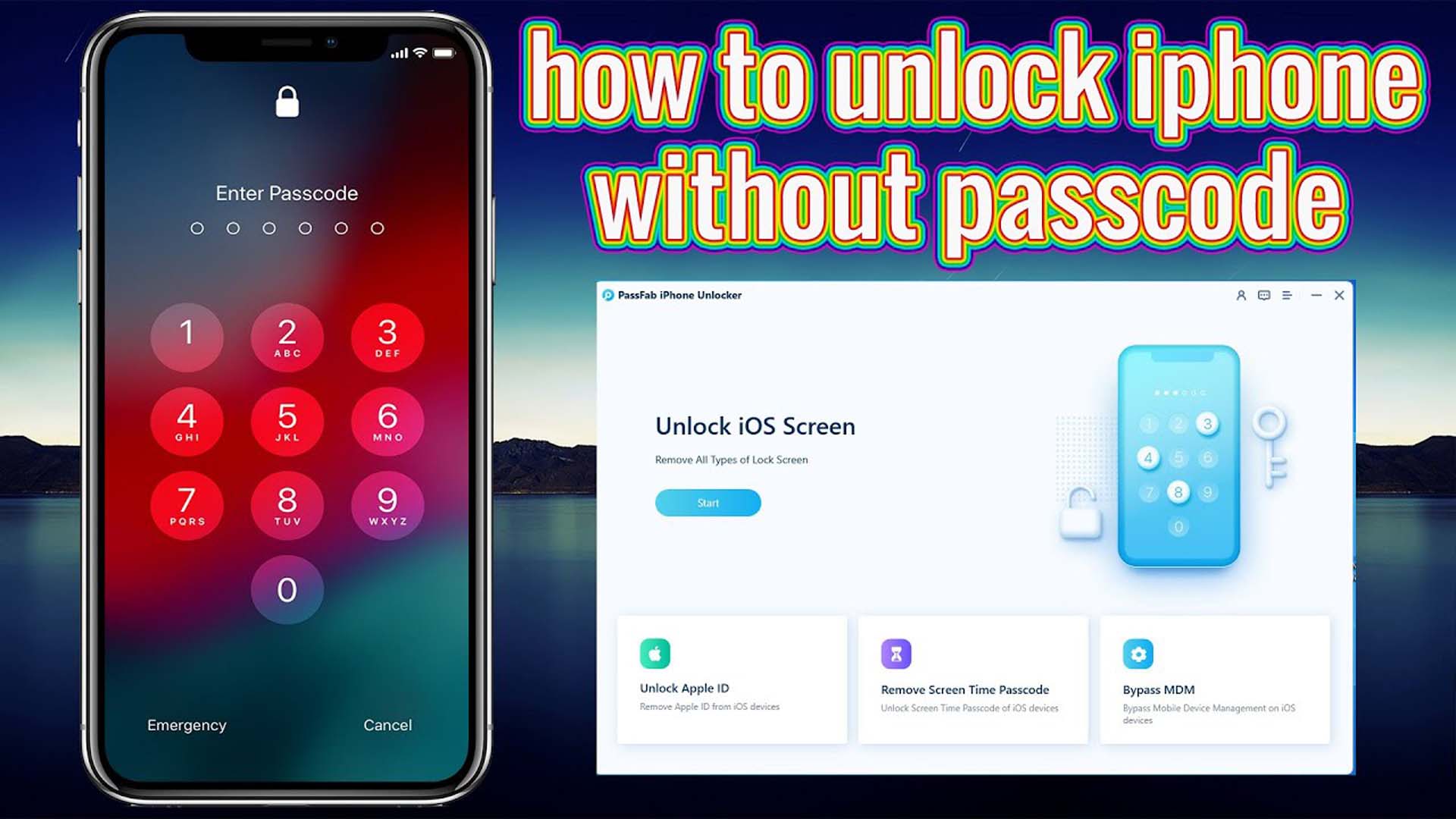
“Unlockt Me” refers to a hypothetical tool or technique aimed at bypassing the security measures implemented on Apple’s iPhone devices. While the specific details of such a tool are not publicly known, it is generally understood to involve exploiting vulnerabilities or weaknesses in the iPhone’s operating system (iOS) or its security protocols.
Methods and Techniques
“Unlockt Me” could potentially employ various methods and techniques to bypass iPhone security, depending on the specific vulnerabilities exploited. These methods might include:
- Exploiting iOS vulnerabilities: This approach involves leveraging known or previously unknown flaws in the iOS operating system to gain unauthorized access to the device’s data and functionalities. These vulnerabilities could range from buffer overflows to race conditions or logic errors in the system’s code.
- Modifying the device’s boot process: “Unlockt Me” might attempt to alter the iPhone’s boot sequence, allowing it to bypass the standard security checks and load a modified version of iOS or a custom operating system. This could grant access to the device without requiring user authentication.
- Physical access and hardware manipulation: In some cases, “Unlockt Me” might require physical access to the iPhone and involve manipulating hardware components, such as the device’s internal memory or the SIM card reader. This method is generally more complex and potentially irreversible.
Potential Risks and Vulnerabilities
The use of “Unlockt Me” carries significant risks and vulnerabilities, which could have severe consequences for the iPhone user and their data:
- Data loss and privacy breaches: Bypassing iPhone security through “Unlockt Me” could expose sensitive personal information, including passwords, financial data, and private communications, to unauthorized access. This could lead to identity theft, financial fraud, or other forms of cybercrime.
- Device instability and malfunction: Attempting to bypass iPhone security through “Unlockt Me” could lead to device instability, crashes, or permanent damage. This could render the iPhone unusable and require costly repairs or replacements.
- Security compromises: Using “Unlockt Me” could compromise the overall security of the iPhone, making it more susceptible to malware infections, data breaches, and other security threats. This could result in the loss of control over the device and its data.
Ethical and Legal Implications
The use of “Unlockt Me” raises significant ethical and legal concerns. Bypassing security measures on iPhones, even with the owner’s consent, can have unintended consequences, potentially jeopardizing the privacy and security of the device and its data.
Ethical Considerations
Using “Unlockt Me” to access an iPhone without the owner’s explicit permission is ethically problematic. It undermines the fundamental principle of respecting individuals’ privacy and control over their personal information. This tool can be misused to access sensitive data like personal messages, photos, financial information, and other private files.
“The ethical implications of bypassing security measures on a device without the owner’s consent are clear: it violates the user’s right to privacy and control over their personal information.”
Legal Ramifications
The legal consequences of using “Unlockt Me” for unauthorized access to an iPhone vary depending on the jurisdiction and the specific circumstances. In many countries, accessing someone’s device without their permission constitutes a criminal offense, such as hacking or unauthorized access to computer systems.
“Using “Unlockt Me” to access an iPhone without the owner’s consent can lead to legal repercussions, including criminal charges for hacking or unauthorized access.”
Unlocking your iPhone can feel like a real head-scratcher, right? But hey, at least you can spice up your phone with some awesome wallpapers! How about a sleek Porsche 918 to make your screen pop? Check out these Porsche 918 wallpapers for iPhone and get ready to impress. Once you’ve got that sorted, maybe we can tackle that iPhone unlock situation together.
Comparison to Other Security Bypass Tools
“Unlockt Me” shares ethical and legal concerns with other security bypass tools, such as password cracking software and rootkits. While these tools may have legitimate uses, they can also be exploited for malicious purposes, leading to unauthorized access and potential harm.
“The ethical and legal issues surrounding “Unlockt Me” are similar to those associated with other security bypass tools, which can be misused to gain unauthorized access to systems and data.”
Security Measures and Countermeasures

Apple employs robust security measures to safeguard iPhones from unauthorized access. These measures aim to protect user data, privacy, and device integrity. However, “Unlockt Me” attempts to circumvent these security measures, posing a significant threat to iPhone security.
Security Measures Implemented by Apple
Apple implements various security measures to protect iPhones from unauthorized access. These measures include:
- Secure Enclave: A dedicated processor within the iPhone that handles sensitive data like encryption keys, Touch ID, and Face ID, isolating it from the main operating system. This ensures that even if the main system is compromised, the sensitive data remains secure.
- Hardware-Level Security: iPhones incorporate hardware-level security features, such as Secure Boot, which prevents unauthorized software from loading at startup. This ensures that only trusted software, authorized by Apple, can run on the device.
- Data Encryption: Apple encrypts user data at rest, meaning it is scrambled and unreadable without the correct decryption key. This makes it difficult for unauthorized individuals to access sensitive information stored on the device.
- iOS Updates: Apple regularly releases iOS updates that include security patches and bug fixes, addressing vulnerabilities that could be exploited by malicious actors. These updates are essential for maintaining the security of iPhones.
- Two-Factor Authentication: Apple encourages users to enable two-factor authentication, requiring them to enter a code from a trusted device in addition to their password when logging in to their Apple ID. This significantly reduces the risk of unauthorized access to user accounts.
- Find My iPhone: This feature allows users to remotely locate, lock, or erase their iPhones if they are lost or stolen. It also helps prevent unauthorized access by enabling a “Lost Mode” that disables access to the device’s data.
Bypass Attempts by “Unlockt Me”
“Unlockt Me” aims to bypass these security measures by exploiting vulnerabilities in iOS, the iPhone’s operating system. These vulnerabilities could include:
- Software Bugs: Exploiting software bugs or vulnerabilities in iOS to gain unauthorized access to the device’s system or data. These bugs could be present in the operating system itself or in third-party apps.
- Hardware Exploits: Utilizing physical hardware exploits to bypass the Secure Enclave or other hardware-level security features. This could involve manipulating the hardware components or accessing the device’s memory directly.
- Social Engineering: Employing social engineering tactics to trick users into granting access to their devices or revealing sensitive information. This could involve phishing attacks, malware, or other deceptive techniques.
Countermeasures to Mitigate Risks, Unlockt me bypass iphone
To mitigate the risks associated with “Unlockt Me,” Apple and iPhone users can implement several countermeasures:
- Regular Software Updates: Installing the latest iOS updates promptly is crucial to address known vulnerabilities and security flaws. Apple continuously releases security patches and updates to address vulnerabilities that could be exploited by “Unlockt Me” or other malicious actors.
- Strong Passwords and Two-Factor Authentication: Using strong passwords and enabling two-factor authentication for Apple IDs can significantly reduce the risk of unauthorized access to user accounts. This prevents attackers from gaining access to the device even if they obtain the password.
- Be Wary of Suspicious Apps and Websites: Users should be cautious about downloading apps from untrusted sources or visiting suspicious websites. These sources could contain malware or other malicious code that could compromise the device’s security.
- Use Reputable Security Software: Installing and using reputable antivirus and anti-malware software can help detect and prevent malicious software from compromising the device. These tools can scan for known threats and protect against unknown vulnerabilities.
- Enable “Find My iPhone”: This feature can be used to remotely locate, lock, or erase the device if it is lost or stolen. This helps prevent unauthorized access to the device and its data.
- Hardware Security Enhancements: Apple could consider further strengthening the hardware-level security of iPhones by implementing additional security measures, such as enhanced hardware encryption or tamper-resistant components. These measures would make it more difficult for “Unlockt Me” or other attackers to physically exploit the device.
- Security Research and Collaboration: Apple should actively engage in security research and collaborate with security experts to identify and address vulnerabilities in iOS and iPhone hardware. This ongoing effort is crucial to stay ahead of attackers and maintain the security of iPhones.
User Education and Awareness: Unlockt Me Bypass Iphone
In an era where technology permeates every facet of our lives, safeguarding our digital assets has become paramount. “Unlockt Me” represents a potent threat to iPhone users, underscoring the importance of proactive measures to protect our devices and personal data. This section provides a comprehensive guide to bolstering iPhone security against such attacks.
Safeguarding iPhone Data and Privacy
Maintaining the security of your iPhone is crucial to protecting your sensitive data and privacy. Here’s a set of best practices to implement:
- Enable Two-Factor Authentication (2FA): Two-factor authentication adds an extra layer of security by requiring you to enter a code sent to your trusted device in addition to your password when logging in. This significantly hinders unauthorized access, even if your password is compromised.
- Use Strong Passwords: Employ complex passwords that include a mix of uppercase and lowercase letters, numbers, and symbols. Avoid using easily guessable information like your birthdate or pet’s name. Password managers can help you generate and store strong, unique passwords for each of your accounts.
- Be Wary of Suspicious Links and Attachments: Do not click on links or open attachments from unknown senders. These could be phishing attempts designed to steal your personal information.
- Install Apps from Reputable Sources: Download apps only from the official App Store. Avoid installing apps from third-party sources, as they may contain malware.
- Keep Software Up-to-Date: Regularly update your iPhone’s operating system and apps. Software updates often include security patches that fix vulnerabilities that could be exploited by attackers.
- Enable Find My iPhone: This feature allows you to locate your iPhone remotely, lock it, or erase its data if it’s lost or stolen.
- Be Cautious about Public Wi-Fi: Avoid using public Wi-Fi networks for sensitive tasks, such as online banking or shopping. Public Wi-Fi can be insecure, and your data could be intercepted by attackers.
Keeping Software Up-to-Date
Regular software updates are crucial for maintaining the security of your iPhone. Apple releases software updates to address vulnerabilities and improve the overall performance of the device. Here’s why keeping your software up-to-date is essential:
- Security Patches: Software updates often include security patches that fix vulnerabilities that could be exploited by attackers. These vulnerabilities could allow attackers to gain unauthorized access to your device or steal your personal information.
- Performance Enhancements: Software updates often include performance enhancements that improve the speed and efficiency of your iPhone.
- New Features: Software updates may also introduce new features and functionality to your iPhone.
Using Strong Passwords
Using strong passwords is fundamental to safeguarding your iPhone and its data. Weak passwords can be easily guessed by attackers, leaving your device vulnerable to unauthorized access. Here’s a guide to creating robust passwords:
- Length: Aim for passwords that are at least 12 characters long.
- Complexity: Include a mix of uppercase and lowercase letters, numbers, and symbols.
- Uniqueness: Use different passwords for different accounts. Avoid using the same password for multiple accounts.
- Avoid Personal Information: Do not use easily guessable information like your birthdate, pet’s name, or address.
“Strong passwords are the first line of defense against unauthorized access to your iPhone. Use a combination of uppercase and lowercase letters, numbers, and symbols, and avoid using easily guessable information.”
Future Trends and Considerations

The ever-evolving landscape of iPhone security presents a dynamic interplay between technological advancements, security measures, and the ingenuity of bypass techniques. Understanding these trends is crucial for developing effective countermeasures and mitigating potential vulnerabilities.
Impact of Emerging Technologies
Emerging technologies like artificial intelligence (AI), machine learning (ML), and quantum computing will significantly influence the security landscape. AI-powered security systems can analyze vast amounts of data to detect anomalies and predict potential attacks, while ML algorithms can adapt to evolving threats and improve detection accuracy. Quantum computing, with its potential to break current encryption algorithms, poses a significant challenge for future security measures.
Key Considerations for Future Research and Development
The evolving nature of iPhone security demands ongoing research and development to stay ahead of emerging threats. Key considerations for future research include:
- Developing advanced authentication mechanisms: Exploring alternative authentication methods beyond traditional passcodes and facial recognition, such as behavioral biometrics or multi-factor authentication, can enhance security.
- Strengthening hardware security: Implementing robust hardware security measures, such as secure enclaves and tamper-resistant hardware, can make it more difficult for attackers to exploit vulnerabilities.
- Improving software security: Regularly updating software with security patches and employing secure coding practices are essential for mitigating vulnerabilities.
- Enhancing user education and awareness: Educating users about common security threats and best practices can help them avoid falling victim to scams and phishing attacks.
- Collaborating with security researchers: Encouraging responsible disclosure of vulnerabilities and fostering collaboration with security researchers can help identify and address security flaws before they are exploited.
FAQ Resource
Is Unlockt Me Bypass iPhone legal?
Using Unlockt Me bypass tools without proper authorization is generally illegal and can result in serious legal consequences.
How can I protect my iPhone from Unlockt Me attacks?
Keep your iPhone software up to date, use strong passwords, avoid downloading apps from untrusted sources, and be cautious about clicking suspicious links.
What are some examples of Unlockt Me bypass techniques?
Examples include exploiting vulnerabilities in iOS, using jailbreaking tools, or attempting to bypass the passcode lock screen.
What are the potential consequences of using Unlockt Me bypass tools?
Consequences can include data loss, privacy violations, legal penalties, and damage to your device’s reputation.